Another LockIT Pro Lock manual but this is a more secure, revised version they say ;) :
You learn that:
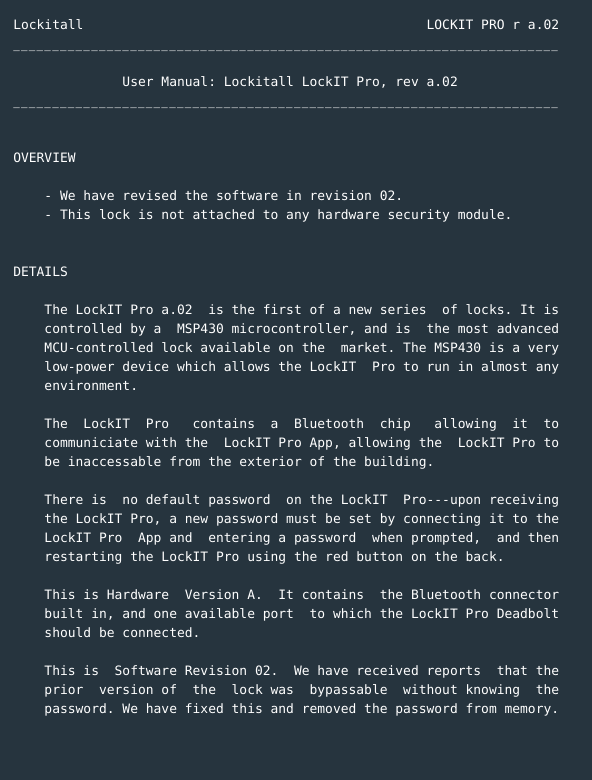
- The lock is not attached to a HSM(Hardware Security Module).
- The password is now not stored in memory.
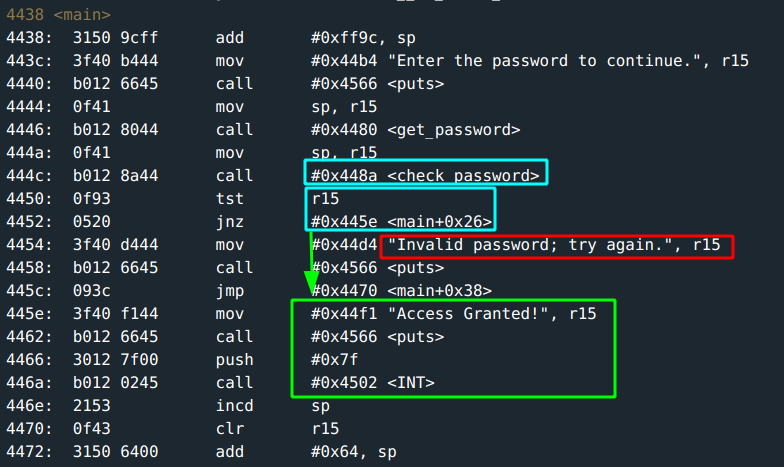
This is how the main function looks like:
There is a check_password function called. You do the usual quick run of the program using a dummy input test, set a breakpoint on check_password and follow through the flow.
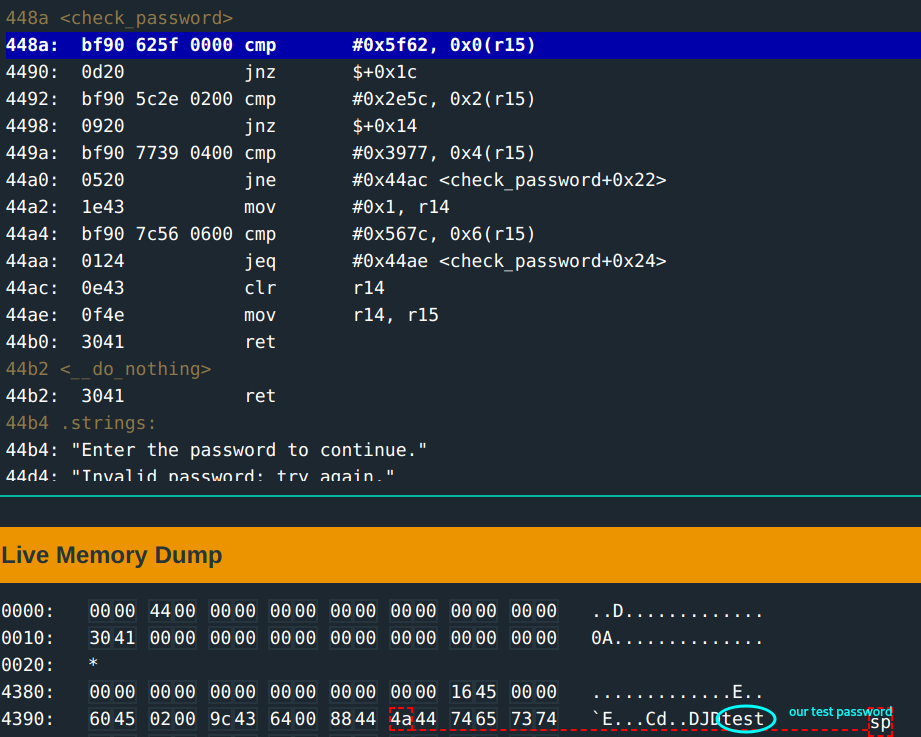
The input test gets stored at address 0x439c.
In the check_password function:
- There are a bunch of comparisons done on the bytes of the input with hex values. This could definitely be the password bytes, you infer.
In pseudocode:
r15 = 0x439c
r14 = 0
if *(r15+[0-1]) != 0x5f62 || *(r15+[2-3]) != 0x2e5c || *(r15+[4-5]) != 0x3977 || *(r15+[6-7]) != 0x567c {
r14 = 0
r15 = r14
return
} else {
r14 = 1
r15 = r14
return
}
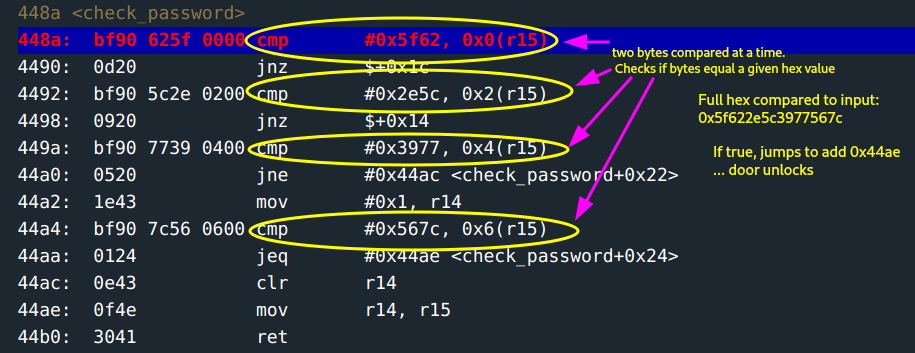
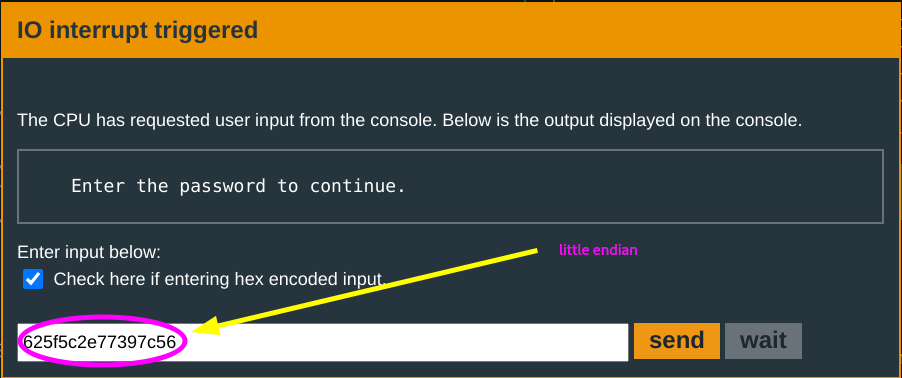
Compare every two bytes of the input to the hex values
0x5f62,0x2e5c,0x3977and0x567crespectively. If any of this is not equal, clearr14(set it to zero) and return. If they match, setr15=r14= 1.
Falling back to main, the call to unlock door happens only if r15 is not zero.
You now put in the correct input bytes:
Open Sesame!!
You fly to Hanoi :D.