Military-grade security lock they say. Here is the manual:
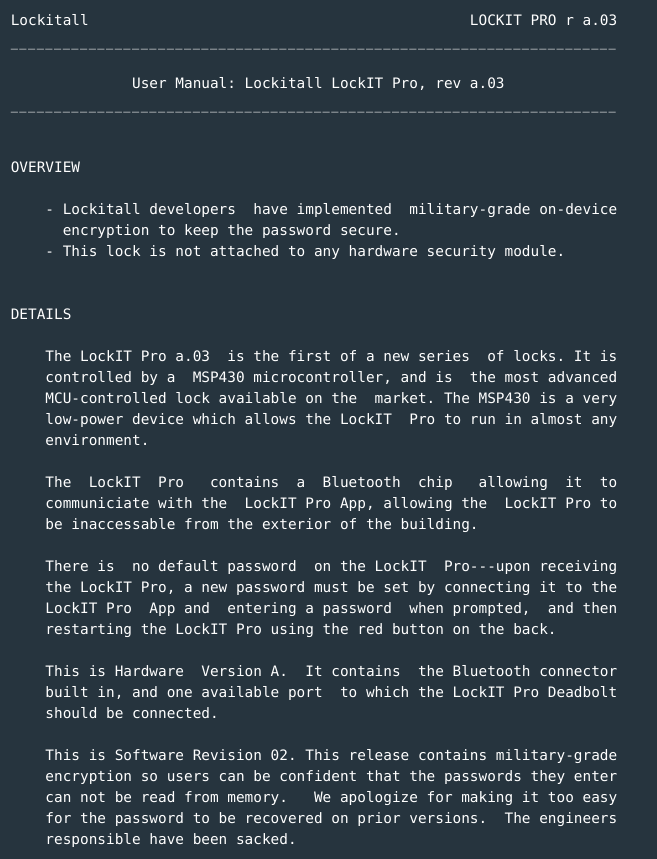
- This lock is not attached to any HSM module.
- Military-grade on-device encryption has been implemented to keep the password secure.
- Passwords entered cannot be read from memory.
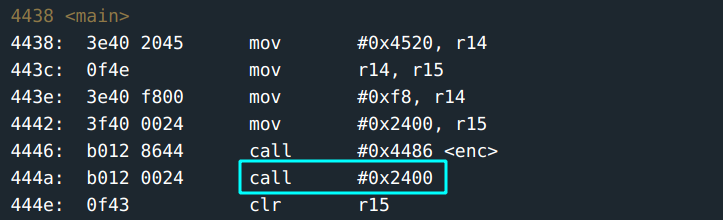
This is the main function:
Interesting findings:
- A block of opcode:
- beginning from
0x4520 - spanning for
0xf8
- beginning from
is passed to enc function. The destination of the result is set for #0x2400.
The enc function basically interchanges the opcode for the one destination to the other using some operations to determine the address (you decide to save the details for this; you can inspect it later).
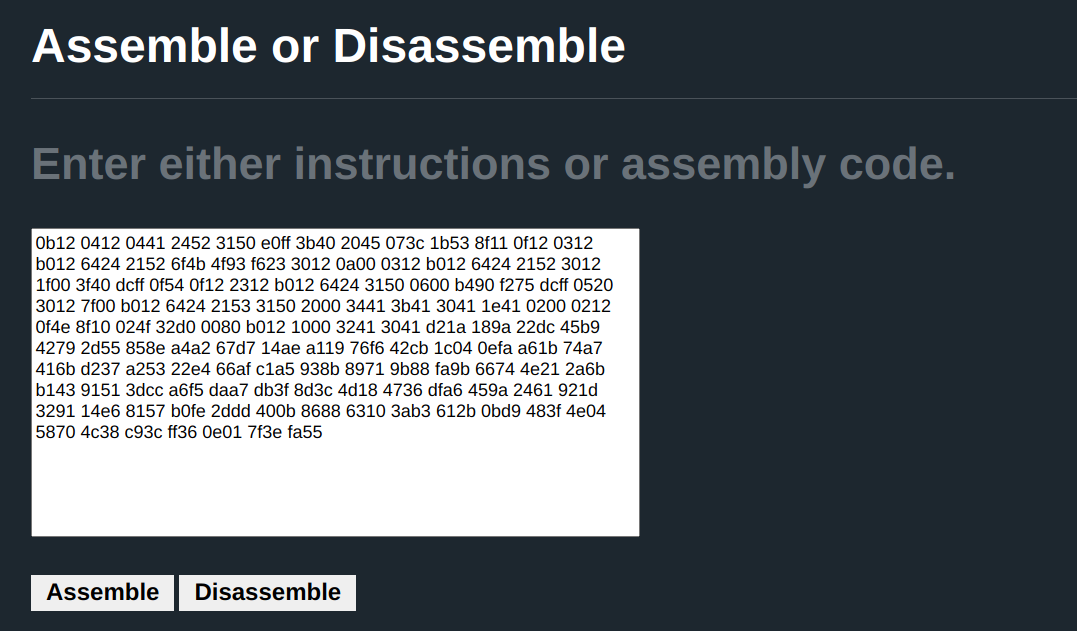
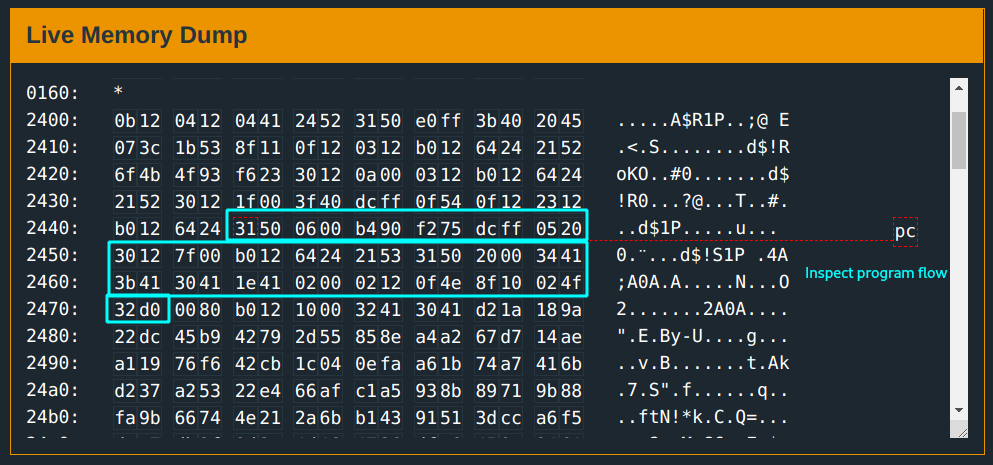
You focus on the memory dump. You can disassemble the block from #0x2400 and follow through…
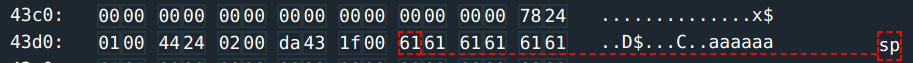
but let’s make things easier. You run the program and put in a test input aaaaaaaa
This gets stored at #0x43da.
Instead of stepping and reading an opcode at a time(this is painfully slow), a better way is to disassemble the the block just after the call to get the input.
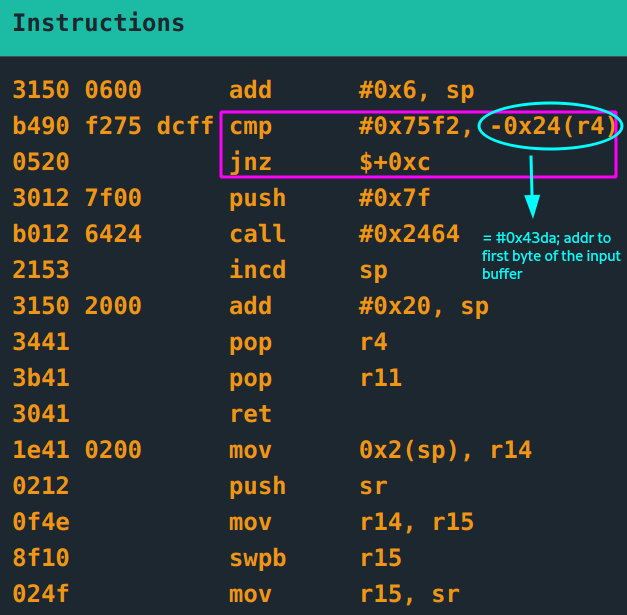
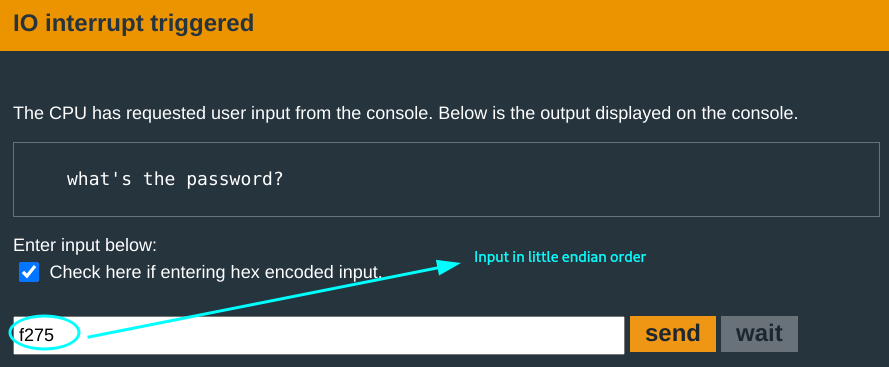
if *0x43da == 0x75f2{
// unlock door
push 0x7F
call INT
}else{
exit program
}
The first byte of the input is compared to value #0x75f2. If equal, unlock door :)
Sweet!! Shall we? ;D
That was one hekla of a place :)
Ride on! To Whitehorse and beyond.