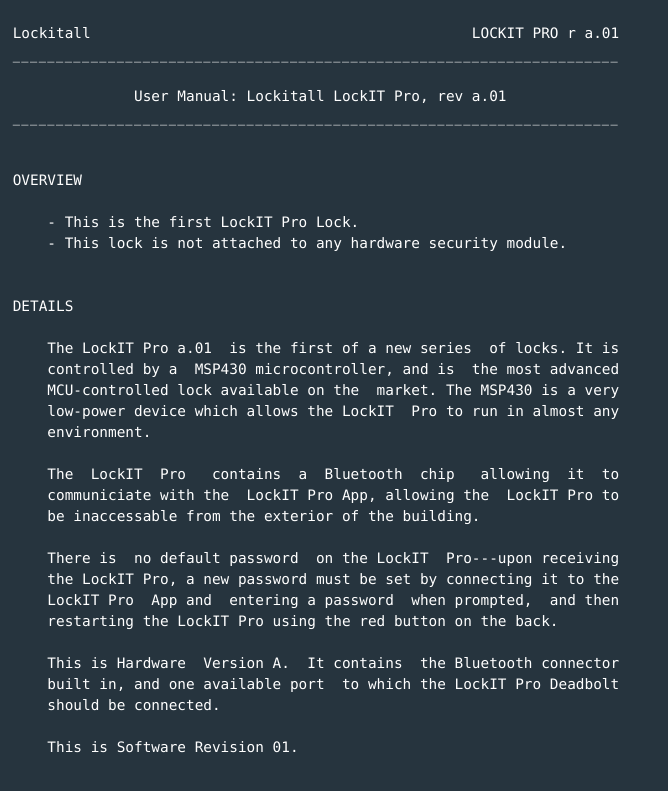
You find a manual for the LockIT Pro Lock:
You learn some things from the manual:
- It is not attached to a HSM module.
- Password set by entering it on the app restarting the lock.
You are presented with a live debugger, a live memory dump, a disassembler and a view of the register states.
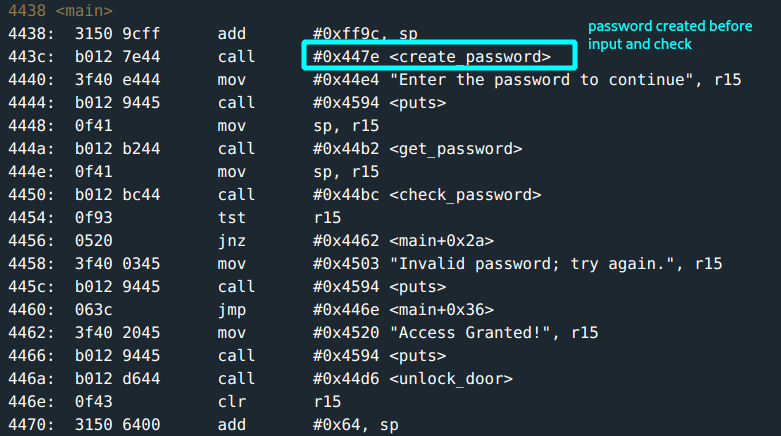
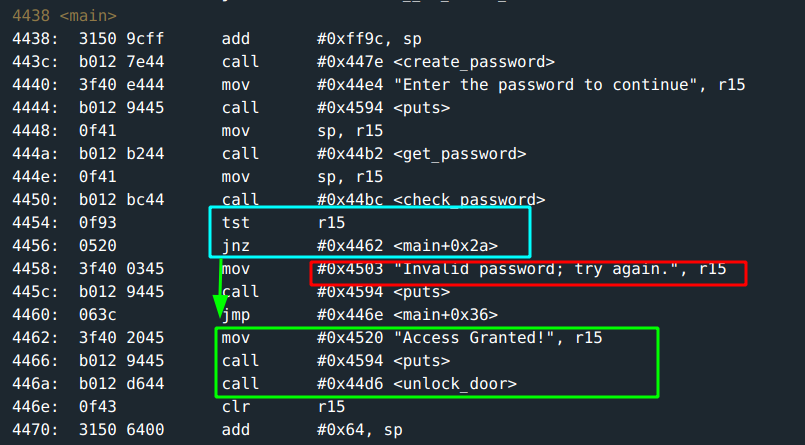
Looking through the main you notice a create_password function that gets called before the input is required or a check for correct input is done.
You do a quick run of the program with a dummy input test to follow through the flow.
This is how the create_password is like:
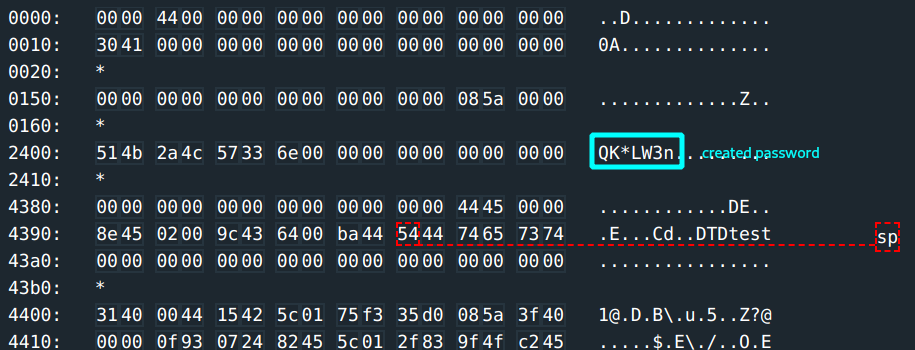
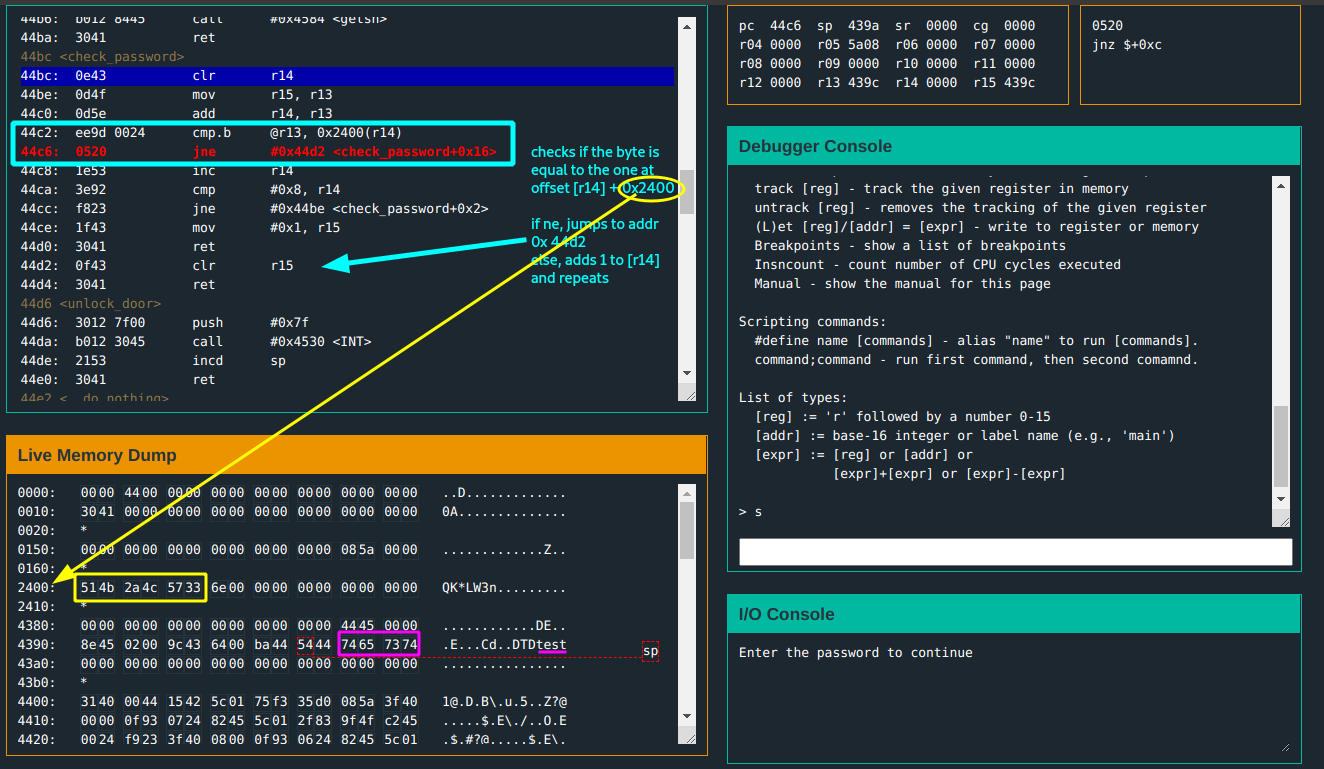
A password is clearly generated and stored at address 0x2400. The input you put in is stored at address 0x439c
So, flowing back through main, create_password generates and stores a password at 0x2400 -> get_password scans and stores user input at 0x439c -> then next instruction calls check_password.
Already there’s a hunch that the created password is what is compared to your input… but you want to see it. :)
In the check_password function:
- A
cmp.binstruction is called for each byte of the input(r13points to the input) and the created password.
In pseudocode:
r14 = 0
r13 = 0x439c
for r14 != 8{
r13 += r14
if *r13 != *(0x2400 + r14){
r15 = 0
return
}
r14++
}
r15 = 1
return
Keep comparing the byte of the input at index(r14) to the byte of the created password at index(r14). If they are not equal, clear r15(becomes zero) and return. If they are equal, repeat for each byte until 8(this is the required length of the password). Set r15 to 1 and return.
Falling back to main, only if r15 is not zero does the door unlock.
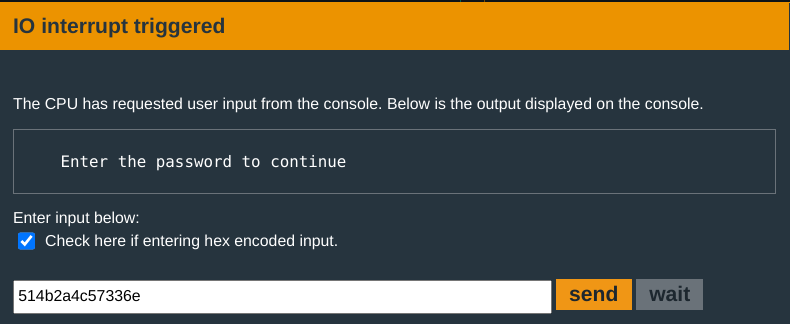
You now put in the correct input: the created password:
And the door unlocks to you!!
Off to Sydney :)