At this point in the journey, you expect a manual to greet you:
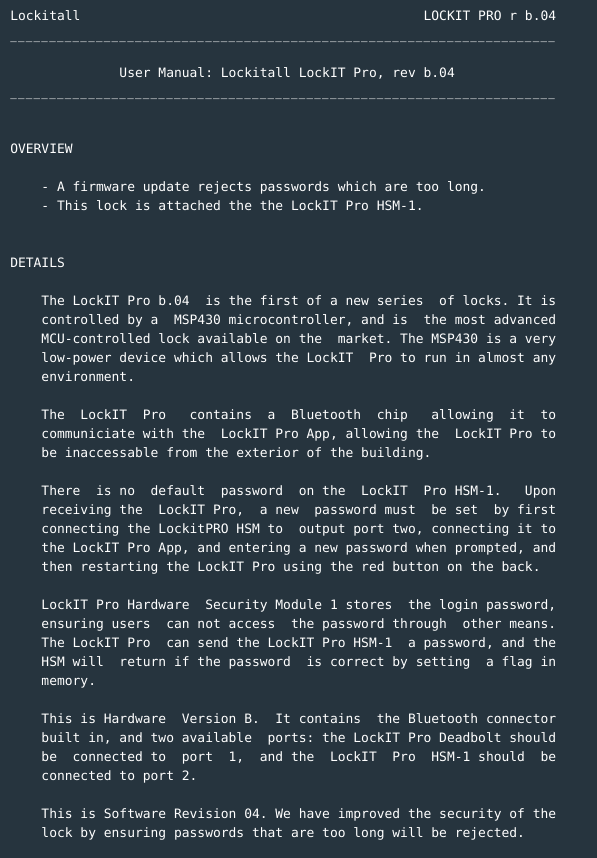
- The lock is attached to HSM-1 module.
- Passwords that are very long are rejected. Just how long is too long?
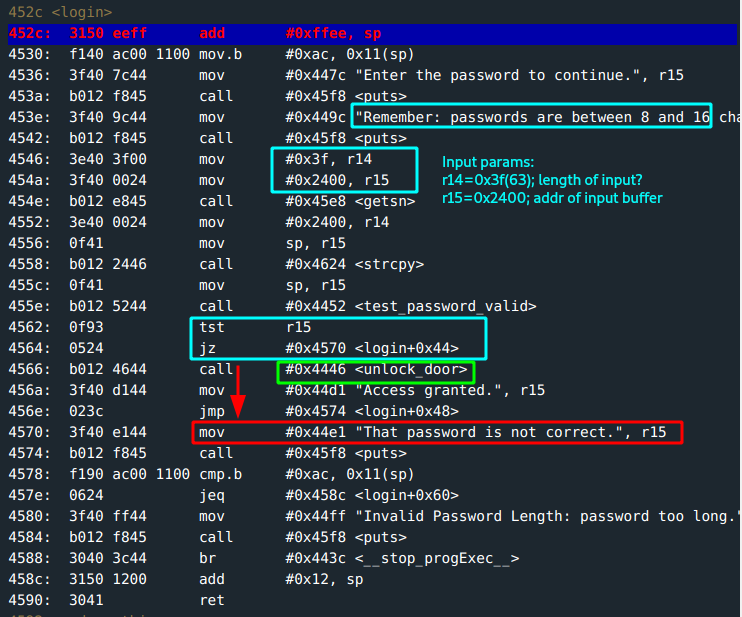
The main function just calls login.
The prompt states the password range should be within
8 - 16characters long. However, from the input parameters of thegetsnfunction:r14: Holds length of the input buffer;0x3f(63)characters. This is more than the one prompted. Clue #1.r15: Holds the address to store the input buffer;0x2400.
The input is copied to
#0x43ee.The copied text is then passed to
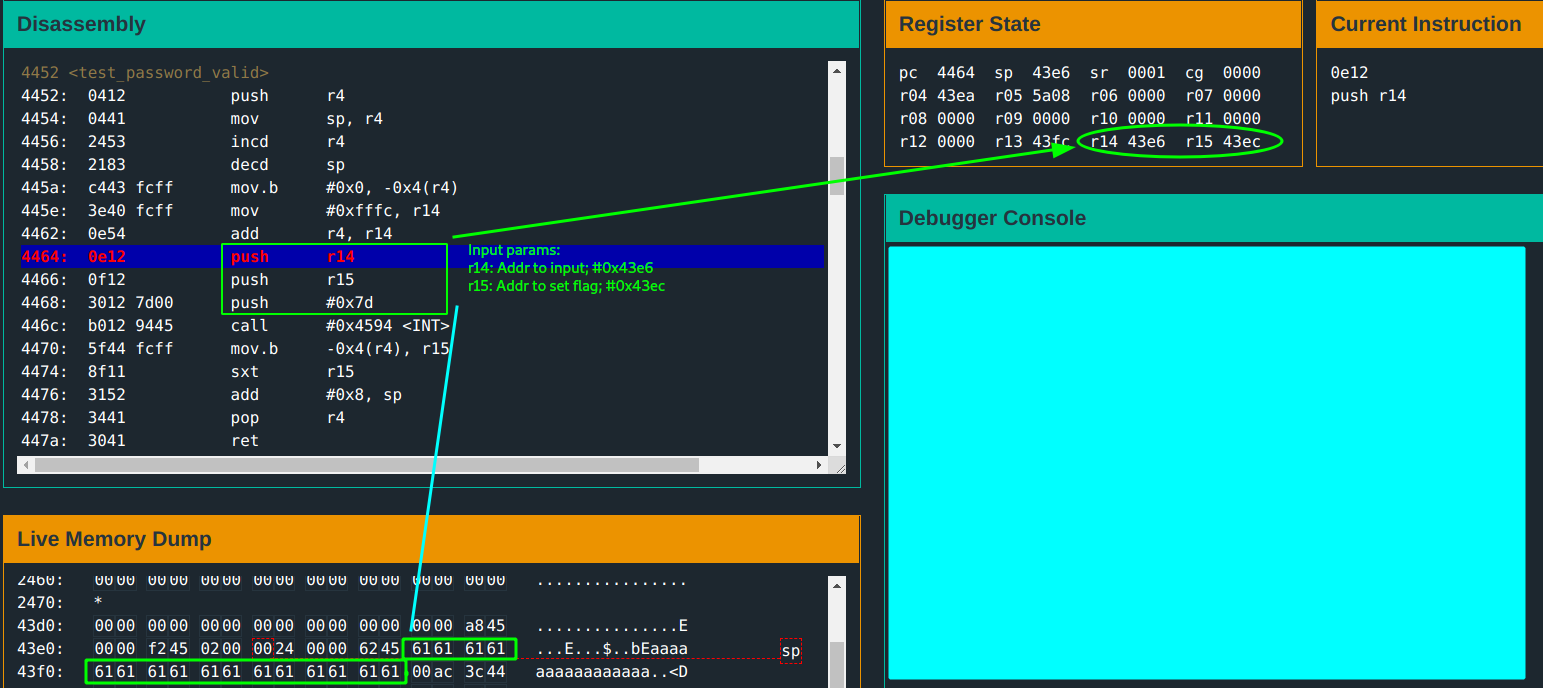
test_password_validfunction; a flag is then set which is tested and the call tounlock_dooris made if it is not zero.Observe:
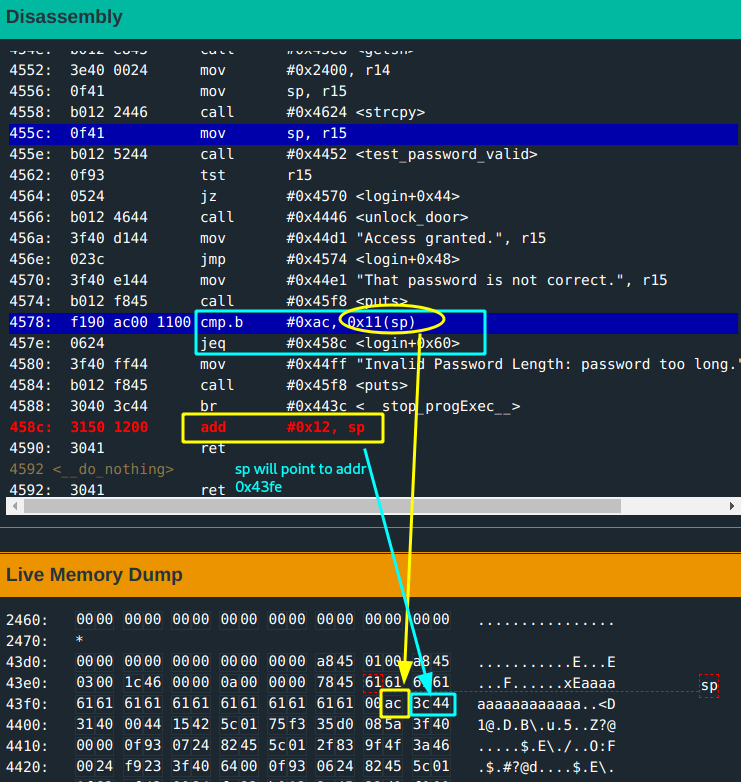
cmp.binstruction. A value at address0x11(sp)is compared with the bytes#0xac. If not equal, the program exits before loading return address. Clue #2Observe: the return address is held at address
add #0x12, sp. Possible overwrite| Clue #3.
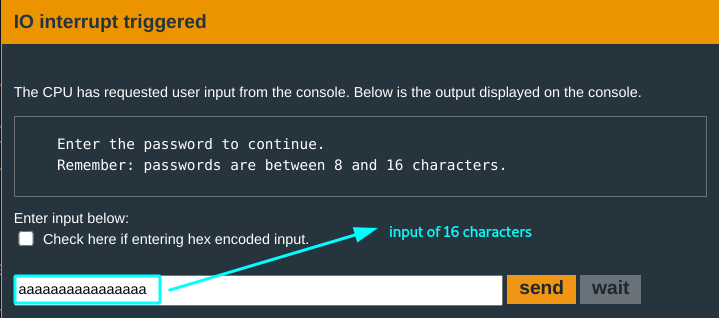
You do a quick run with a test input aaaaaaaaaaaaaaaa:
Looking through the test_password_valid you only notice the call to INT 7D and the flag is set at #0x43e6
The test input obviously fails, however..
- The return address is held at the
17th -18thbytes of the input. - The byte that gets compared to
0xacis the 16th byte of the input.
You are tasting the victory now!
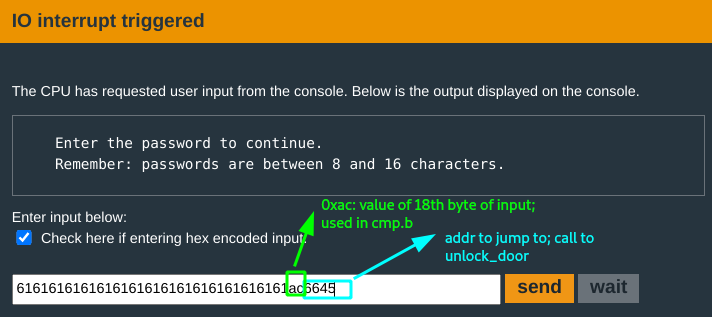
All that is left is to craft the input; the address you want to jump to is the call to unlock_door which is at #0x4566.
Who rocks? You do!
Ready for Montevideo! :D