You get to Hanoi, you find a manual.
Things are a bit different this time:
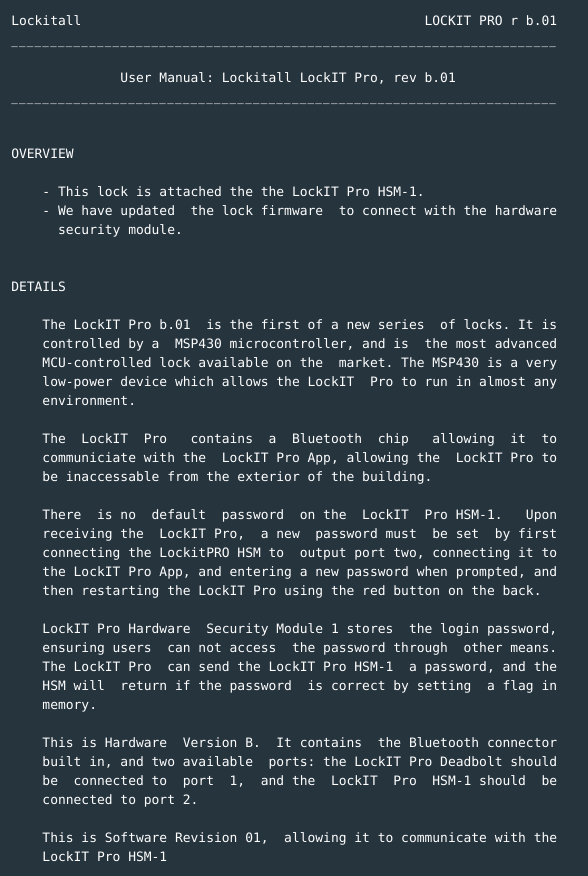
- This Lock is attached to LockIT Pro HSM-1.
- Password stored in the HSM.
- Password set by connecting to app through the HSM and restarting the Lock.
- A flag is set by the HSM after validating a correct password input.
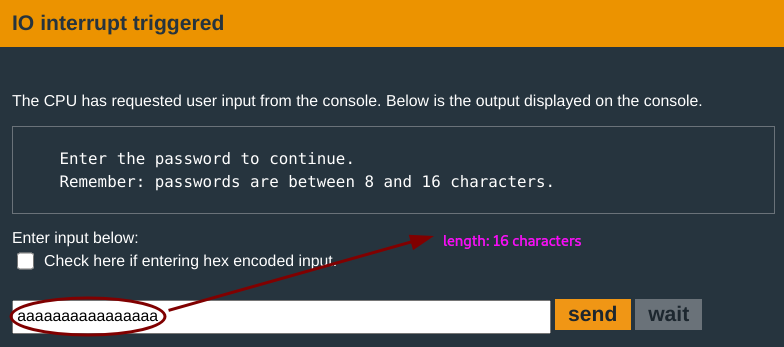
The main function just calls the login function. The prompt for writing your test input gives an interesting clue: the password range.
You input a test password aaaaaaaaaaaaaaaa of length within the specified range and set a breakpoint at login and test_password_valid to follow through the flow.
- Fron the manual, the
getsnfunction takes two params:
// length limits input buffer length
void gets(char *buf, unsigned int length)
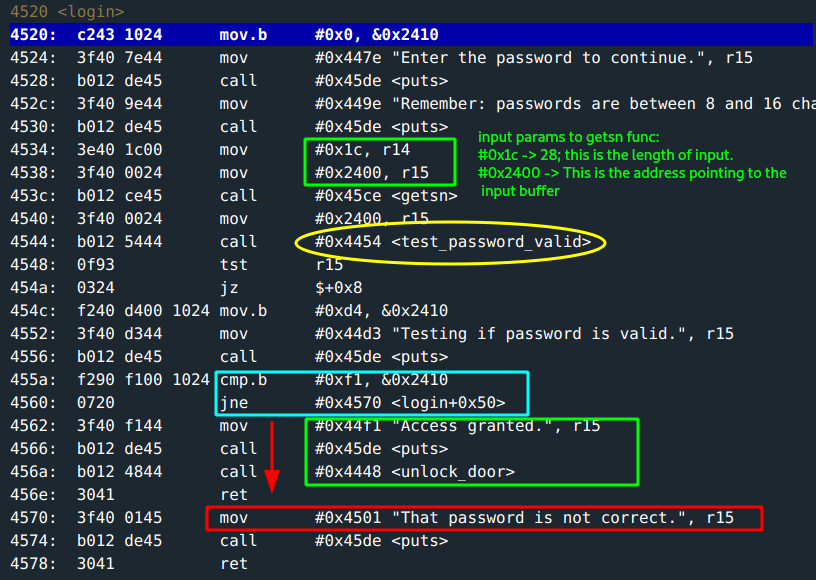
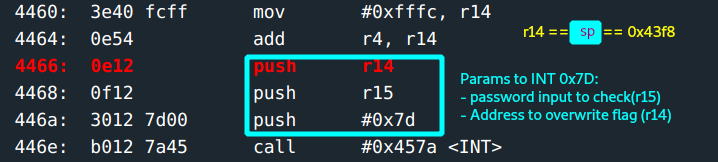
r15holds the address that points to the input buffer(where the input would be stored).r14holds the input length0x1c. This is 28; which is waay more than the specified range limit of8 - 16 bytes. This quacks like opportunity :)
After input, the test_password_valid gets called.
This function basically, makes a call to INT 0x7D to test password validity and sets flag value.
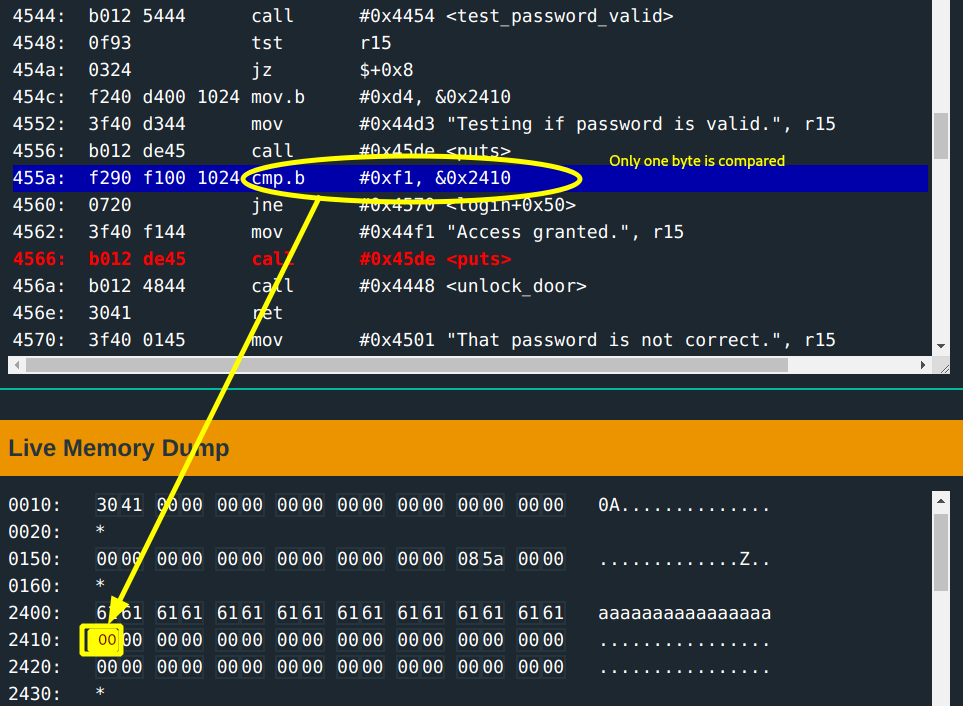
Moving along, the flag does not get set so r15 is 0 on test 15 in the login function. This causes a jump to address 0x455a where there is a cmp.b which determines whether to call unlock_door. Interesting.
- Only one byte is compared, the byte at address
0x2410; this is the first byte after a 16-byte input.
if *0x2410 == 0xf1{
print("Access granted")
call unlock_door
}else{
print("That password is not correct")
ret
}
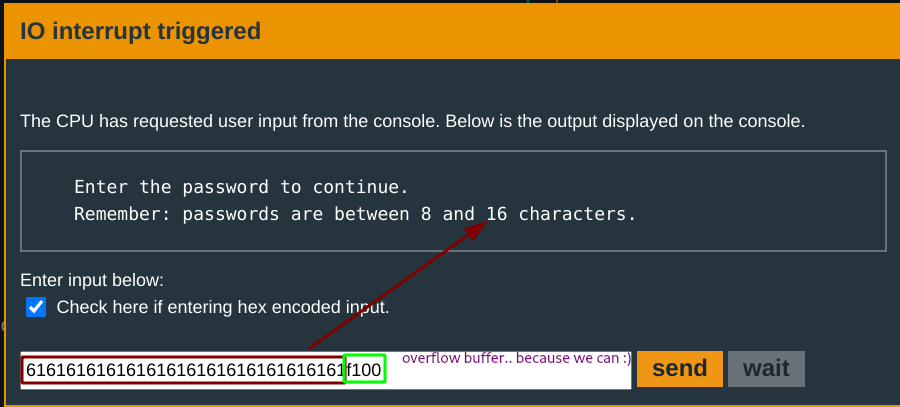
Since you know the input buffer does not restrict input to a length of 16, you can have a longer input with the 17th byte being f1. Easy!
Wide open! :)
To Cusco or To Reykjavik… you decide!