You get to Addis Ababa and find a lock with a manual:
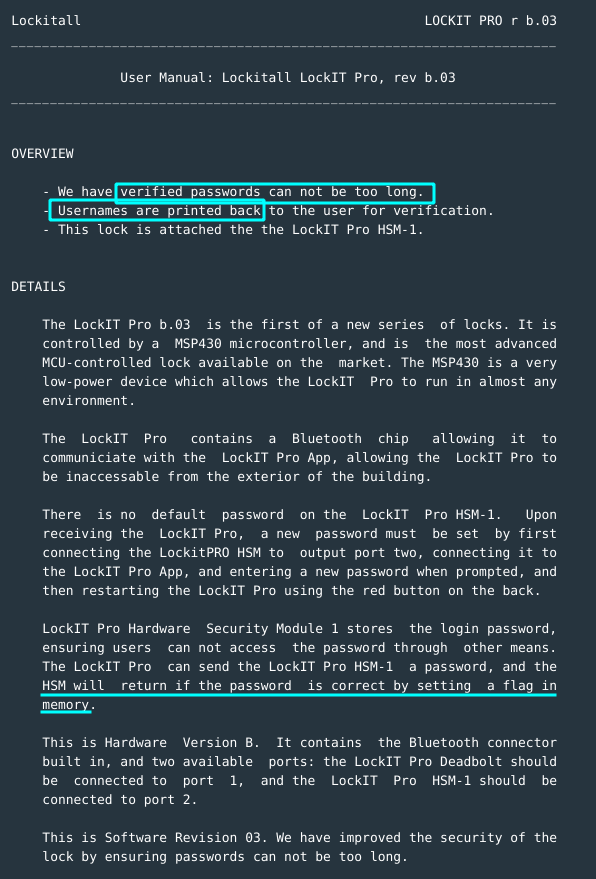
- The lock is attached to HSM-1 module.
- Passwords cannot be too long.
- Usernames are printed back.
- Flag set in memory if password is correct.
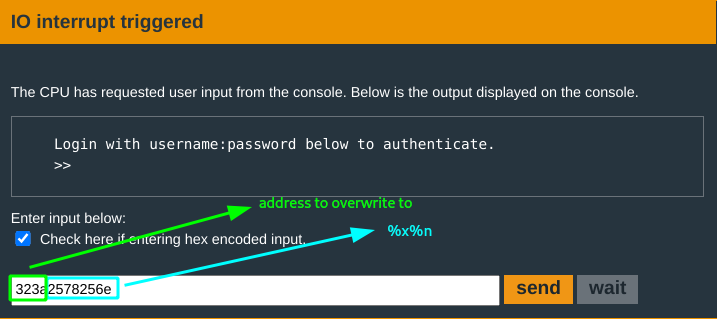
Usernames are printed back. This must be a clue. You think of format string vulnerabilities. Note to self: Printf!!
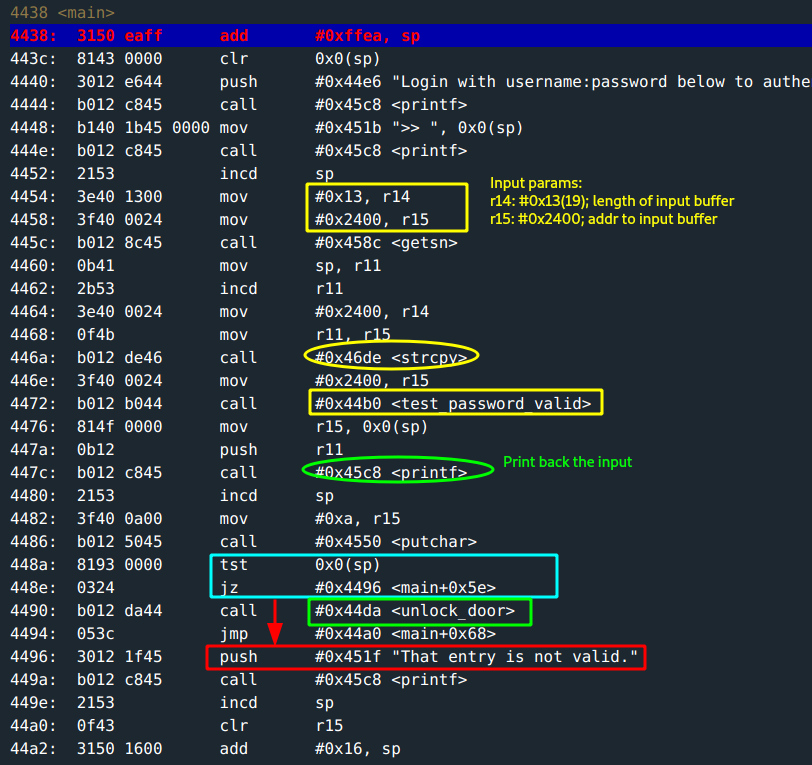
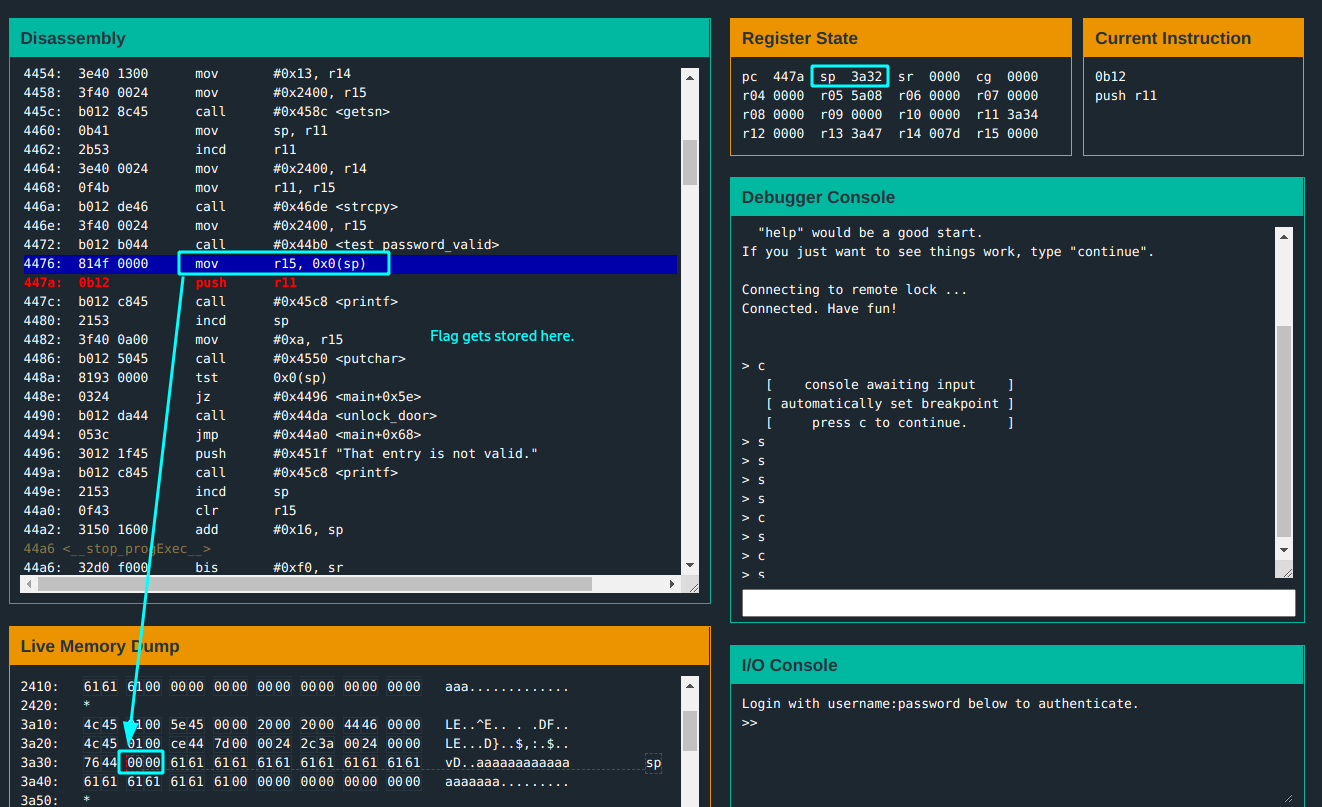
This is the main function:
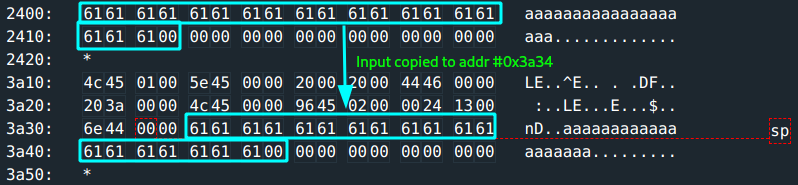
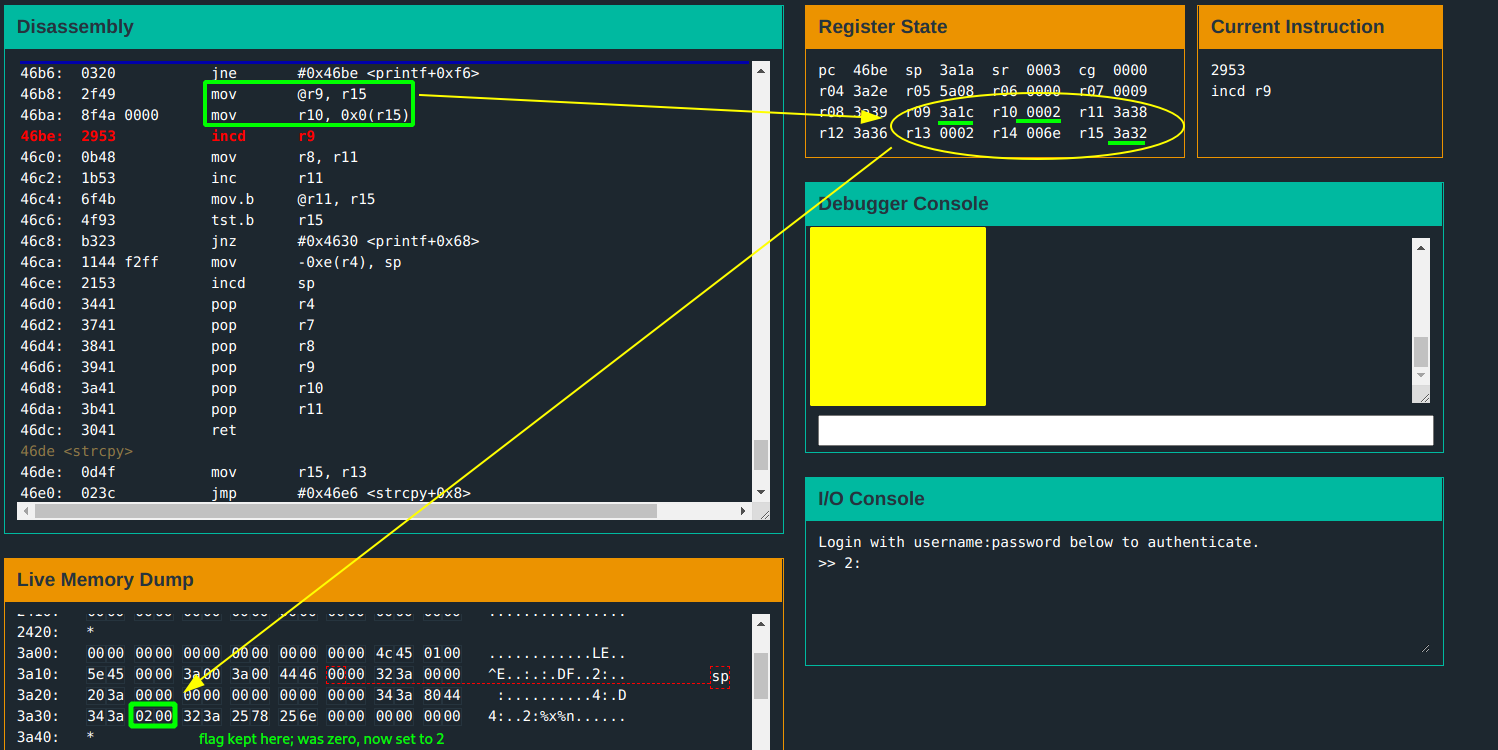
r14: the length of the input buffer is#0x13(19)characters.r15: the input buffer is at address0x2400.- The input is copied to another destination at address
0x3a34. - The input is then passed to
test_password_valid; a flag is set depending on whether the password is correct. - The copied input is then printed back using
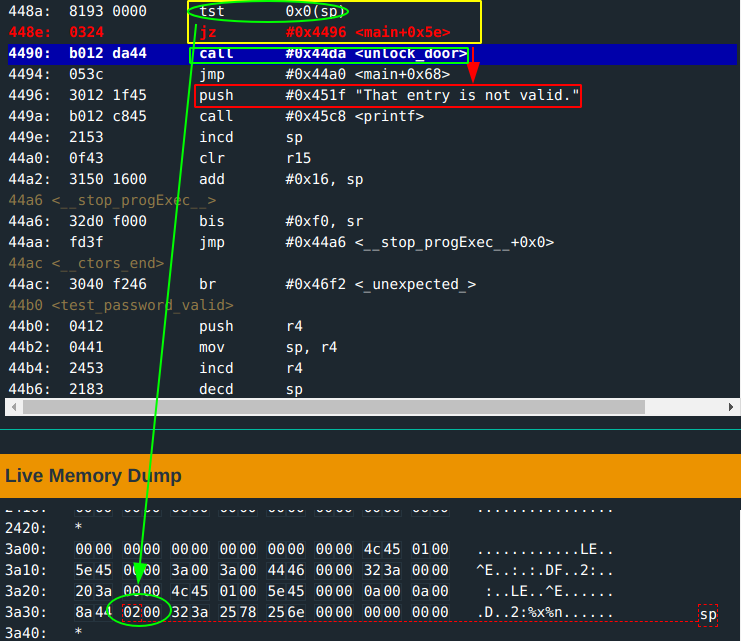
printf. tst 0x0(sp)checks if flag is set before call tounlock_door.
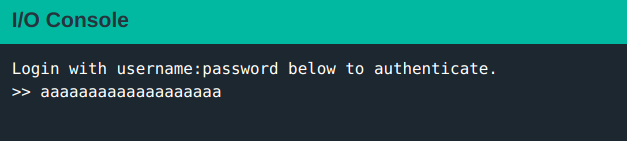
A quick run with test input: aaaaaaaaaaaaaaaaaaa (19 characters) to study program flow.
The test_password_valid function:
The flag gets set at address 0x3a32; the test input is wrong so flag is not set.
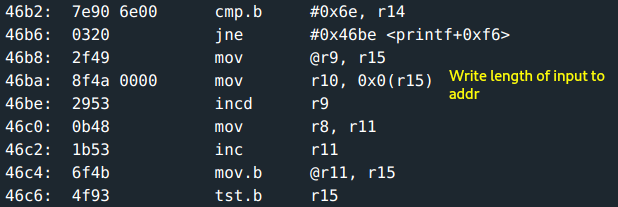
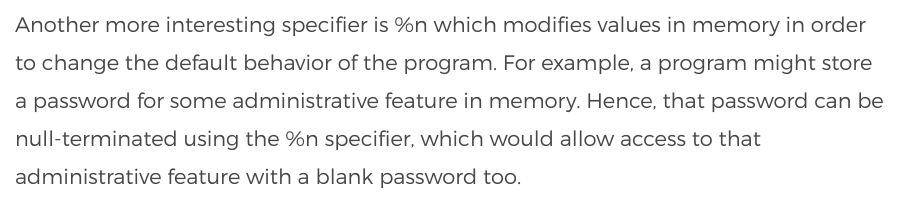
The input is printed out as is. The printf function is bulky but basically, it also checks for format specifiers: %s, %x, %nand displays accordingly. This presents an exploitable vulnerability. A look at %n:
- The length of the input gets written to memory at an address in the
1st- 2ndbyte of the input. Interesting. %xwrites the argument in hex notation.
Detour:
Read more about format string vulnerability here.
The following, is relevant snippets for this particular task.
This can be exploited to overwrite a value in memory… but where to write to? The address where the flag gets set! The door gets unlocked when the flag is not zero.
Flag not zero: call to unlock_door… Hello!
Jo cannot wait no more! _0/