Background: Krypto kidnapped none other than Professor Smoke himself!
Mission: Use the graph-matching tool to figure out if an attack on the KDA network happened.
For all the marbles: What machine was compromised.
Graphs! and schnitzels.. at the end.. maybe?
What we know
- All requests to the KDA network flow through: Gateway machine before taking a journey through various Backends until they finally reach the Admin.
- Requests get split to sub-tasks executed on the BE or Admin.
- Each machine undergoes periodic vulnerability scans.
Treasure hunt
Find a request or any of its sub-tasks that reached a vulnerable Admin machine, with the Gateway and Backends also being vulnerable.
Into the woods!
Let us analyze our data first and prepare it before graphing.
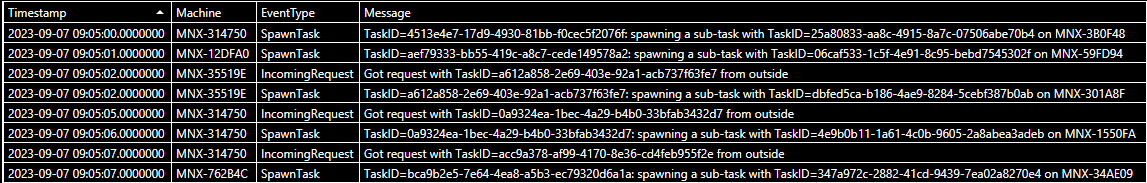
MachineLogs
| take 50
MachineLogs
| distinct EventType
**# -- EventType -- #**
# IncomingRequest
# SpawnTask
# PeriodicScan
- Find the machines that were found to have vulnerabilities during the scans:
let VulnMachines = MachineLogs
| where EventType == "PeriodicScan"
| parse Message with MachineType:string " periodic scan completed, " VulnCount:long *
| where VulnCount > 0
| distinct Machine, MachineType
| take 100
- Let’s figure the vulnerable machines that received requests and grab task IDs.
let HotMachines =
MachineLogs
| where EventType == "IncomingRequest"
| lookup kind=inner VulnMachines on Machine
| parse Message with * "TaskID=" TaskID:guid *;
- Let’s figure the vulnerable machines that spawned request tasks to other machines and grab child machine and child task IDs.
let Spawners =
MachineLogs
| where EventType == "SpawnTask"
| lookup kind=inner VulnMachines on Machine
| parse Message with * "TaskID=" TaskID:guid * "TaskID=" ChildTaskID:guid * "on " ChildMachine;
What we have. From identifying all the vulnerable machines, we divided into a set that received requested and a set that spawned requested and to which machines.
Now, we need to find a request that passed from through a chain of vulnerable machines (from a gateway machine to an admin machine).
Spawners
| make-graph TaskID-->ChildTaskID with HotMachines on TaskID
| graph-match (gateway)-[backend*1..25]->(admin)
where gateway.MachineType == "Gateway" and target.MachineType == "Admin"
project Start=gateway.Machine, End=admin.Machine, path=backend.Machine
💡 This challenge sent me on rabbit holes while attempting to prepare the data for graphing. Major thanks to hints from Liesel Hughes that streamlined my thought process.